We all know about computer viruses. We’ve heard about that, and most of us have managed to make that Someone Else’s Problem. We have an automated process, or an IT team, that updates our anti-virus programs. We know we shouldn’t open email attachments from people we don’t know. We know about checking that web sites use https.
But we’re ignoring the biggest liability in security.
It’s not the software. It’s not the hardware. It’s what the geeks call the wetware: human beings. In other words, you. And the banks and credit card companies are largely to blame.
It’s Good To Talk
Ever had a phone conversation like this?
You: Hello?
Them: Hello Mr Smith, it’s Joe Jones from X bank here. Mr Smith, we’ve detected some unusual activity on your account and I just wanted to check with you that it is genuine. Did you make a purchase for £2,399.99 on the XYZ website yesterday?
You: No, no I didn’t!
Them: Ah, OK, we suspected there might be a problem, but don’t worry, you won’t be charged. For security, could I take characters 2 and 4 of your password?
You: Er, that’s a and p.
You’ve just given some security information to – well, who? The follow up call that you’re promised will also need some security information, but it won’t be characters 2 and 4 again. The reason this type of scam is so successful, of course, is because it exactly follows the process that many banks and credit card companies use.
Here’s a quote from the website of a credit card company:
“Before you ever give a stranger your personal or financial details over the phone, make sure you know who they are.”
They don’t explain how this magic – being “sure” that you know who a “stranger” is – is achieved. I’ve tried this:
Them (allegedly): Hello Mr Edmunds, it’s Fred Smith from X credit card here. I need to discuss a potential issue with your account, so can I just take you through security first?
Me: But I don’t know who you are.
Them: Sorry Mr Edmunds, I’m Fred Smith from X credit card.
Me: And I’m Keith Edmunds. Where do we go now?
Some of the banks are slowly improving. A common question I ask now is, “Before I tell you my security information, tell me something about my account that isn’t common knowledge.” Some will respond positively to that.
Personal Information
The real problem, of course, it that their workflow is insecure and common practice. But it’s not just calls that allege to be from banks.
“Hello Ms X, it’s Joe Jones from the tax office here. We’ve received your notification about Simon Smith starting work with you, but there’s some confusion over his home address. Could you just confirm that for me?”
Must be genuine! How else could they know Simon had just started working for you? Apart from Facebook and LinkedIn, that is?
The answer here is simple: “confirm” means “verify that something is correct”. So yes, you can confirm it: what address do they have?
We all know not to reveal confidential information in emails. That’s because email is inherently insecure – but there are ways around that. Here at Tiger Computing, we all receive our payslips by email, but it’s encrypted email that can only be read by the person it’s intended for.
Some of the financial institutions implement their own “secure email” on their website. Of those, some will send an email to your normal address telling you that there’s a new “secure” message on their site: that’s helpful. Others refuse to send such messages, citing security concerns. That’s stupid.
Green Light
We all know that, when we go to that institution’s site to read the secure message, we should check for the “green padlock” in the address bar, because that tells us the site is secure, right? Not quite. It tells us that the data that passes between our browser and that site is encrypted, which is a good thing. It does not offer any guarantee at all that the site is who they say they are.
What you should look for is what is technically known as an Extended Validation certificate.
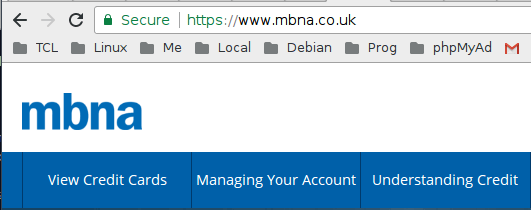
MBNA is a bank that provides credit cards. Here’s the address bar of (allegedly) their website:
Compare that with First Direct:
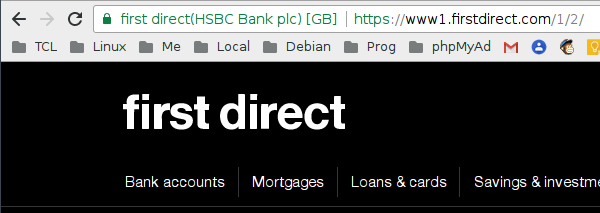
The difference is that First Direct use an Extended Validation certificate, and thus name of the legal entity that operates this website – in this case, HSBC Bank plc – appears in green in the address bar.
MBNA uses a Domain Validated certificate, which proves that the person applying for the certificate has some control over the mbna.co.uk domain (but doesn’t verify in any way who they are).
You are much more justified in trusting the First Direct site than the MBNA one, although I should point out that MBNA do say: “However and whenever you use your credit card or contact us, your security is our priority.” So that’s reassuring, eh?
Extended Validation Certificates
Certificates – which are how a site gets the green padlock in the address bar – are issued by Certificate Authorities. Wikipedia explains the process that a Certificate Authority must follow before it may issue an Extended Validation certificate:
- Establish the legal identity as well as the operational and physical presence of website owner.
- Establish that the applicant is the domain name owner or has exclusive control over the domain name.
- Confirm the identity and authority of the individuals acting for the website owner, and that documents pertaining to legal obligations are signed by an authorised officer.
A Quick Lesson In Ethology
A fundamental principle of animal behaviour is that you will get more of the behaviour you reward.
We are being rewarded by the financial institutions – including those who make our security their priority – for behaving badly.
They reward our bad behaviour (giving characters 2 and 4 to strangers over the phone) by giving us a reward (“protecting us from fraud”). Oh, the irony!
They reward our bad behaviour of accepting Domain Validated certificates by giving us what we want (access to our account).
Every time you reward bad behaviour, you reinforce it.
Let’s Change The World
No one is talking about this.
So let’s start talking about it. Let’s tell people how some financial (and other) institutions are teaching us bad habits.
There are three policies that institutions need to implement if they want to discuss confidential information with us in a responsible way:
- The Caller Must Authenticate First: when you call your bank, it’s reasonable for them to ask you for characters 2 and 4, or whatever they do. You called them: it’s almost certainly really them, and they don’t know you are who you say you are.
When they call you, it’s reasonable for them to give you some information to prove who they are (which will be the first such institution to let you ask for characters 2 and 4 of their password?) . They called you: it’s almost certainly you who has answered, and you don’t know they are who they say they are. - Websites Must Have Extended Validation Certificates: tell your friends, and even your not-too-serious enemies. Complain to your bank and credit card companies when they try to fob you off with a cheap Domain Validated certificate. Better still, vote with your feet and find an organisation that does this properly.
- Use Encrypted Mail: yes, it does exist and it is secure. It is easy to use, but I would accept that it is not as easy to set up as it should be. However, if the banks (etc) start offering to send encrypted mail, it will reach a tipping point and, ultimately, be ubiquitous.
While we wait for those institutions to improve, make sure that your friends, acquaintances and staff are not leaking secure information to that nice man from – well, anywhere.
Further Reading
- For “social engineering”, including many examples of where fraudsters have been able to find out confidential information, I recommend “The Art of Deception” by Kevin Mitnick. I especially recommend it if you think you would never fall for such a scam.
- Wikipedia explains Domain Validated certificates and Extended Validation certificates.
Could this article be improved?
Let us know in the comments below.



